One of the coolest features I like about AWS is it not only gives you the powerful images through AMI but also allows you to import your VM images running in your data center as well. In this, I would like to show you how simple it is to import the VM image into the AWS
The prerequisites for VM import are
- Configure the AWS CLI on the VM.A simple How-To guide can be found here in this link https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-getting-started.html
- S3 Bucket in the region you want to import the VM
- IAM Role named VMimport
For S3 Bucket I am assuming name “my-vm-imports”
Creating IAM Role
You cannot create using the AWS management console. You have to follow the aws- only
- create a trust policy trust-policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": { "Service": "vmie.amazonaws.com" },
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals":{
"sts:Externalid": "vmimport"
}
}
}
]
}
2. Using aws command line create a role vmimport
aws iam create-role --role-name vmimport --assume-role-policy-document file://trust-policy.json
3. Create a file named role-policy.json with the following policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation",
"s3:FullAccess"
],
"Resource": [
"arn:aws:s3:::my-vm-imports"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::my-vm-imports/*"
]
},
{
"Effect": "Allow",
"Action":[
"ec2:ModifySnapshotAttribute",
"ec2:CopySnapshot",
"ec2:RegisterImage",
"ec2:Describe*",
"ec2:FullAccess"
],
"Resource": "*"
}
]
}
4. Use the following command “put-role-policy” to the role we created before.
aws iam put-role-policy --role-name vmimport --policy-name vmimport --policy-document file://role-policy.json
Next steps :
- Upload the VM image to S3
aws s3 cp file_path s3://my-vm-imports
2. Create a container file which contains the s3 bucket name, format, description and key name in the s3 bucket. Save this file as JSON
[
{
"Description": “My VM",
"Format": "ova",
"UserBucket": {
"S3Bucket": “my-vm-imports",
"S3Key": "my-vm-imports/myVm.ova"
}
}]
Note: Only OVA,VMDK image formats are supported in AWS
4. Finally, import the image from S3 with import-image command. After that, your image(AMI) will be ready for use
aws ec2 import-image —description “Linux or Window VM” —-disk-containers file://container.json
Thanks for Reading.
Best Regards
CloudTern



 The 5th Generation mobile network, popularly known as 5G, is the new global wireless standard that succeeds the 4G technology. The 5G technology offers high-speed network connectivity with low latency and accommodates a wide range of devices in the network. Today, businesses are aggressively embracing the 5G revolution. However, the majority of businesses are challenged to apply the 5G benefits to operations owing to the exponential growth of digital innovation that is augmented with data-heavy emerging technologies in the form of AI/ML platforms, AR/VR solutions and real-time analytics. The Covid-19 pandemic was a key driver of this digital innovation. This is where private 5G networks make a strong case.
The 5th Generation mobile network, popularly known as 5G, is the new global wireless standard that succeeds the 4G technology. The 5G technology offers high-speed network connectivity with low latency and accommodates a wide range of devices in the network. Today, businesses are aggressively embracing the 5G revolution. However, the majority of businesses are challenged to apply the 5G benefits to operations owing to the exponential growth of digital innovation that is augmented with data-heavy emerging technologies in the form of AI/ML platforms, AR/VR solutions and real-time analytics. The Covid-19 pandemic was a key driver of this digital innovation. This is where private 5G networks make a strong case.
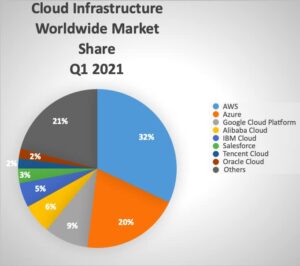 Technology is changing rapidly every year. The year 2021 is no different. However, one thing that remains constant here is the position of AWS in the public cloud infrastructure segment. AWS has been a leader in this segment since its advent.
Technology is changing rapidly every year. The year 2021 is no different. However, one thing that remains constant here is the position of AWS in the public cloud infrastructure segment. AWS has been a leader in this segment since its advent.










 You’ve heard of software as a service (SaaS), Infrastructure as a Service, Platform as a Service, There is XaaS to describe Anything as a Service.
You’ve heard of software as a service (SaaS), Infrastructure as a Service, Platform as a Service, There is XaaS to describe Anything as a Service.
